Full Episode
Steve chat’s with the CEO and founder of Deepfence, Sandeep Lahane, to learn how the company started and what sets it apart from other Cloud Security Workload Protection products.
Company Information

Deepfence is setting a very high bar in the Cloud Native Workload Protection (CNWP) space.
Their mission is to “empower organizations with unparalleled cloud-native security solutions that protect, detect, and respond to evolving threats”
Their offering is purpose built for protecting your internet connected containerized workloads.
Links
The following was mentioned during the episode
- Deepfence – https://deepfence.io/
- Deepfence’s ThreatStryker Sandbox – sign up here
- BPFdoor malware – link
Test Drive – ThreatStryker
I love it when companies have a live sandbox environments that you can play around in!
I will walk you through how to sign up for the sandbox and show you ThreatStryker’s capabilities.
Sign Up
To access Deepfence’s ThreatStryker Sandbox sign up here.
After you sign up you will be presented with your login credentials.
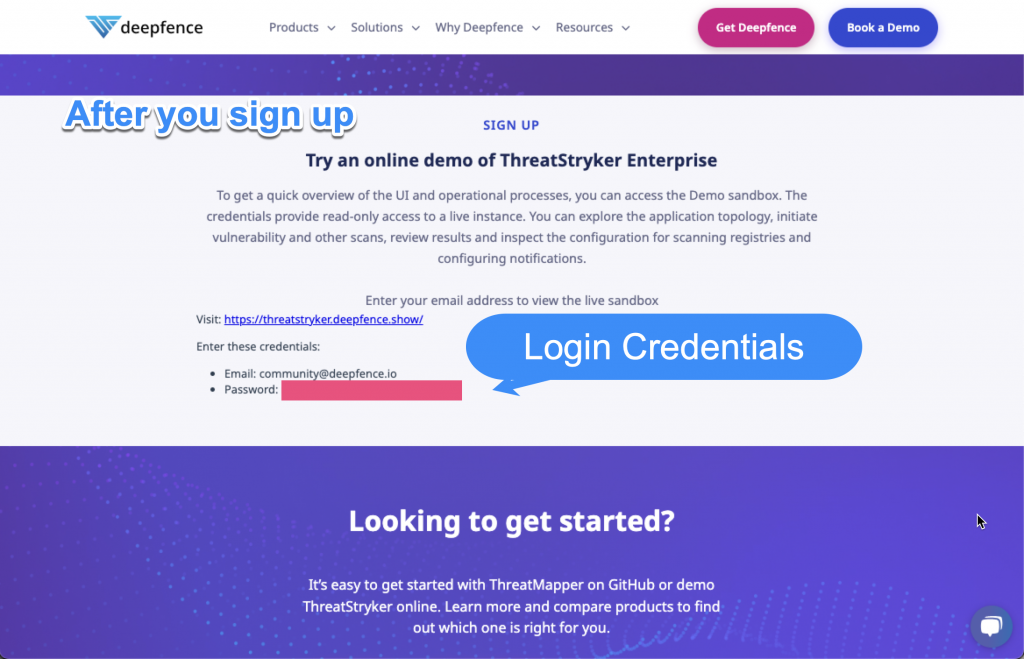
I will be going over some cool stuff that I saw in the Sandbox and providing a hyperlink so you can follow along too.
Login
Navigate to the demo login page – https://threatstryker.deepfence.show/auth/login?redirectTo=%2F
Use the credentials that were assigned to you in the “Signup” section to login
After you sign in you will be brought to the Dashboard
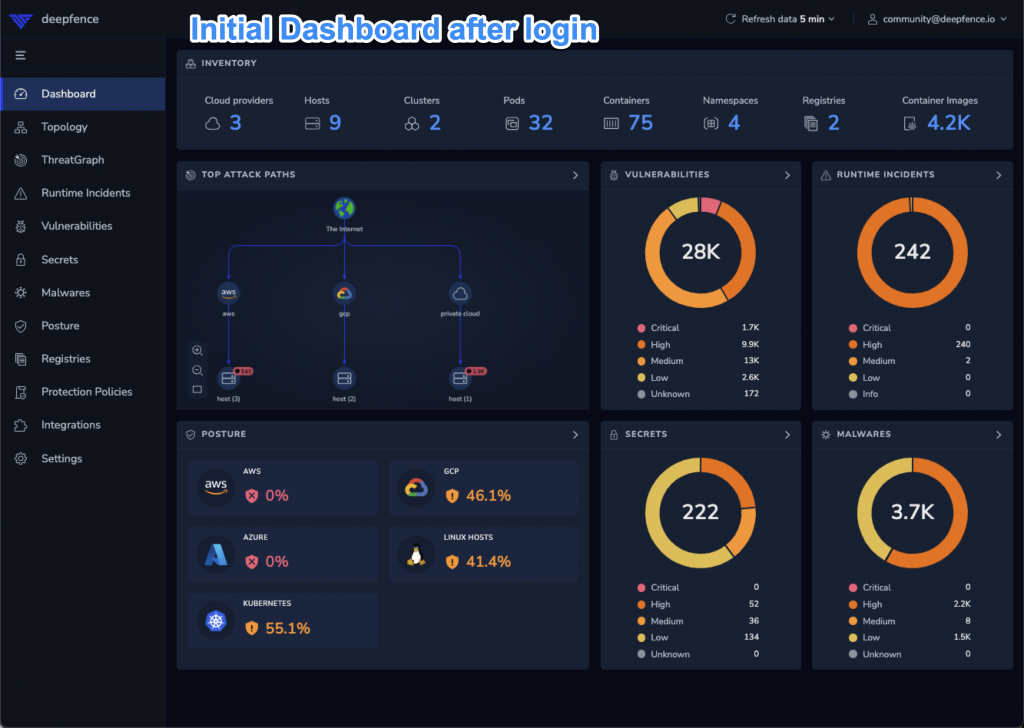
Dashboard
The main dashboard shows the cloud inventory, top attack paths, current posture, and counts (by severity of) vulnerabilities, runtime incidents, secrets, and malware found in the environment.
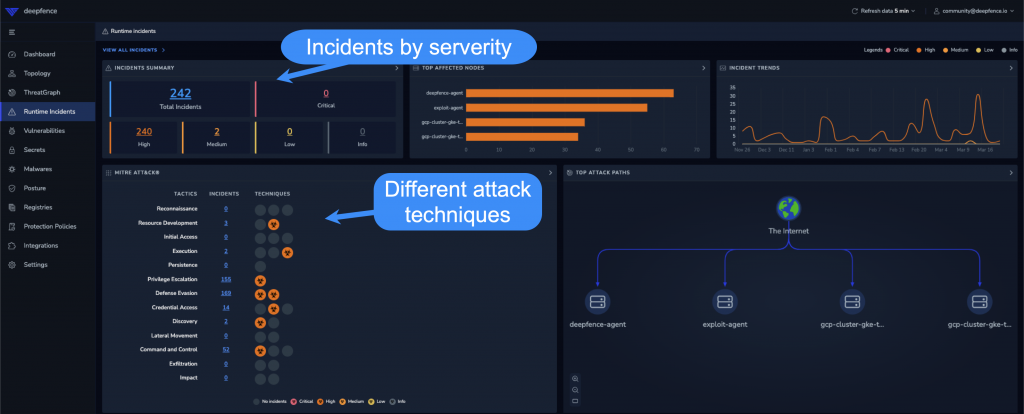
Runtime Incidents
The main dashboard for this section shows you a breakdown of incidents by severity and the MITRE ATT&TCK framework.
https://threatstryker.deepfence.show/runtime-incidents
These are actual attacks on your infrastructure that got past your Web Application Firewall (WAF).
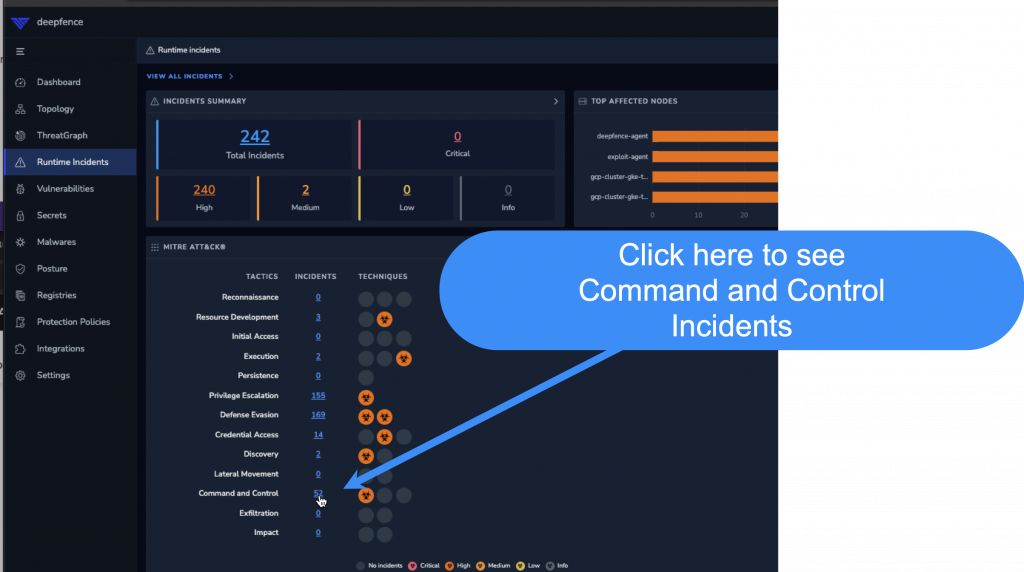
Let’s take a closer look at the “Command and Control” attacks by clicking the hyperlink next to the “Command and Control” line item in the “MITRE ATT&CKS” card.
o execution of shell /bin/sh!

Opening up the alert there is a lot of detail, including the full HTTP body!

This is interesting, but it is unclear is the shell actually executed. I think i may need to check my logs to determine that. Let’s keep scrolling down….
There is a graph showing various hits for different attack techniques… one is a high level alert for Lateral Movement!
LATERAL MOVEMENT ALERT!!!

After double clicking the red dot in the “Lateral Movement” row, we are brought to the Trojan alert details. I love the detail here but i’m not sure if the system actually executed the payload. I would need to look at the system logs


Vulnerabilities
I like that Deepfence shows the most vulnerable attack paths
https://threatstryker.deepfence.show/#/vulnerability/vulnerabilities

Clicking the first item I see that a container is running that is susceptible to the log4j vulnerability.

Topology
This is one of the coolest features of ThreatStryker. An interactive node graph of your environment, including calls to external environments!
https://threatstryker.deepfence.show/#/topology/cloud
Let’s Click some nodes!
AWS Node
It appears that we have a few arrows going to AWS, and AWS is talking to the internet and some third party services.

Hosts Inside AWS
What’s this? We have infrastructure running in AWS?
Three hosts have been discovered:

Double clicking “deepfence-poc-agent-1” reveals three containers running on the host

Container info
Double clicking on the “wordpress_wordpress_1” container reveals some information in the frame on the right of the page. I can see a breakdown of vulnerabilities by severity, a list of processes running, and the docker labels.

Double clicking on the vulnerabilities graphic brings up a list of vulnerabilities for this container

Selecting a vulnerability from the list we get some info

Container Scanning
Scanning containers as they are built and before deployment is always a good idea. Deepfence supports many registries:
https://threatstryker.deepfence.show/#/registry_vulnerability_scan

Integrity Monitoring
You can create custom rules to alert on file modification or access to specific paths on disk
https://threatstryker.deepfence.show/#/topology/cloud


Secrets
I like that Deepfence will look for secrets on the disk of the containers
https://threatstryker.deepfence.show/#/secret-scan/scans
Below is an overview of the secrets found

I click on the Private Key slice
I then bring up a list of findings for one of the containers and find the row I am interested in

The signature found something, but it wasn’t useful as that is the ssh key that runs sshd
